Experts in on-premise telemetry data
Cylynt identifies who is using your software and brings piracy under control.

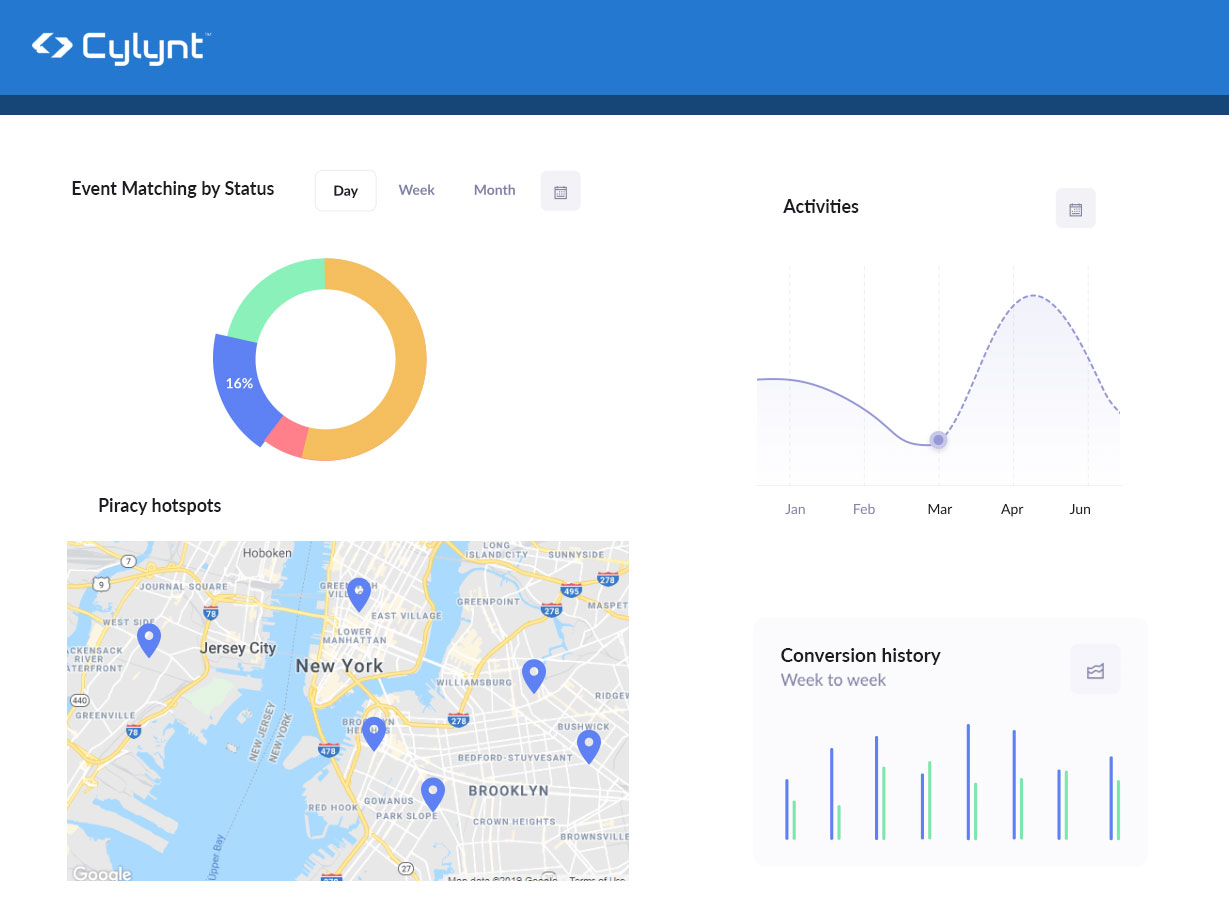

Telemetry Data for the Entire Organization.
Cylynt software helps your company to protect your intellectual property from non-compliance and piracy.
We have the most powerful and useful technology solutions on the market to stop copyright infringements and recover your lost revenue, which can sometimes stretch into the millions.
Complimentary Piracy Impact Reporting
Using our intuitive data gathering tools we find out who is using your software illegally and how much revenue you are losing.
Actionable Data
Providing evidence of mis-use of your licenses should streamline your negotiations with non-compliant customers, but our legal department will provide evidence if you need to take legal action to protect your IP.
Business Intelligence
Cylynt’s business intelligence features help you visualize our data, showing how customers use your software and uncovering technical issues. Your sales team can use our analytics to optimize trial evaluations and successfully renegotiate enterprise license agreements.
License Compliance and Revenue Generation
Cylynt provides the data you need to renegotiate enterprise license agreements with your clients, backed up with evidence of over-deployment of your software or non-compliant sharing of licenses.
Brand Protection
Using the data, you can identify and eliminate counterfeit and cracked versions of your software that could contain dangerous malware, reflecting badly on your brand through no fault of your own.
Ongoing Anti-Piracy Monitoring
We monitor for piracy of your software, as well as alerting you to customers who accidentally overrun their license agreement.
Let's talk
If you would like to take advantage of our solutions, contact us today.
- IE +353 (0)1 513 8640
- US +1 (424) 278-9990